While smartphone keylogger controversy is nothing new, the security of the data collected has shed new light on what may be a severe defect in how that data is stored. Parental monitoring developer mSpy suffered its second data leak in 2018, and millions of user’s information may have been exposed.
What makes the data storage method used by keylogger developers is that many of those smartphone users are minors, and the data captured could potentially be highly personal.
In the U.S. Alone iPhone boasts a user base of over 80% of teens nationwide. Considering that much of the data being exchanged between those devices is stored in iCloud should be a cause of concern for parents and parental monitoring application developers alike.
Privacy & Monitoring Apps
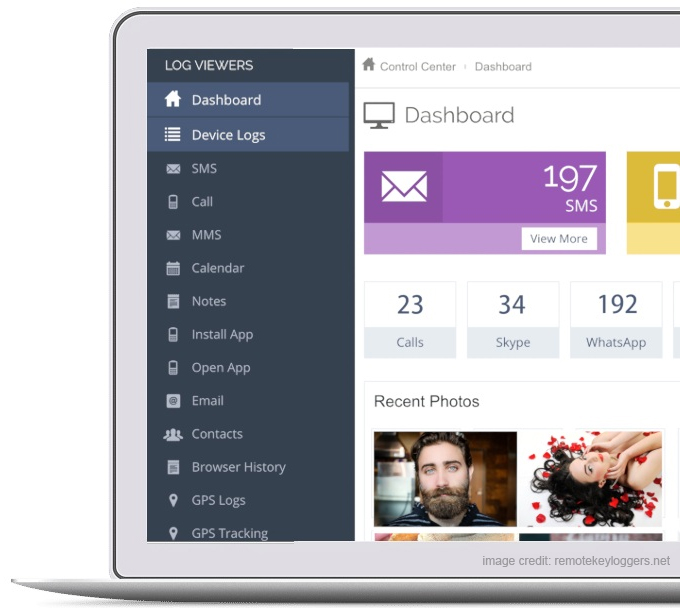
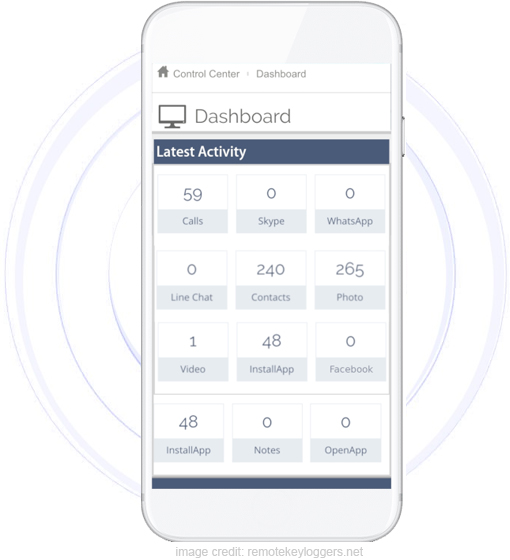
The information captured from iPhone monitoring applications is quite extensive. The information includes GPS locations, iMessages, social network activity, as well as the entire Camera Roll. Considering that hackers don’t actually need physical access to the iOS device in order to connect to iCloud is considered the Achilles heel of these applications.
To keep data safe online it should be encrypted locally before being sent to cloud based servers. iCloud alternatively encrypts the data while it’s in a state of transfer. Either method is relatively secure; the problem however lies when a second stream of data is being sent to the application developer’s servers.
The information needs to remain accessible and readable to the iPhone’s administrator, whether or not there is any encryption at all is hard to say as it must be un-encrypted and sent back to cloud storage where it is stored as human-readable text.
This makes guaranteeing the privacy of iPhone keylogging applications difficult as the information collected is in a constant state of flux. Even worse, the developers themselves do not disclose how their data is stored or transferred.
When visiting the websites of popular parental monitoring application developers such as FlexiSpy, or Remote Keyloggers, an extensive search through their FAQ’s provides no insight as to what security protocols or encryption methods are used to protect the privacy of their client base.
Legal guardians who are considering the use of these types of applications should exercise their due diligence prior to purchasing or installing any type of application that could potentially harm the privacy of their legal wards.
For those that are suspicious that their own iOS devices may contain malware or any type of unapproved monitoring application, one of the easiest methods to prevent further data leaks is to simply change the iCloud credentials.
The vast majority of compromised data on the iPhone is due to negligent password management and loose control over what is being sent to iCloud. It is also prudent to check the phone’s settings to determine how many iCloud accounts it is distributing to.
Quite often when iCloud credentials cannot be obtained, a new account can be created and added to the device. Unknown to the user, the iPhone is syndicating data to more than one iCloud, and looking at the phones settings doesn’t exactly make it clear to novice iPhone owners.
To learn more about iOS and iPhone security visit the developers at Remote Keyloggers and follow their software and security road map as they continue to develop further software and safety applications for iOS devices.




